Phiten Co., Ltd
“We installed MylogStar because we highly evaluated its ability to collect all logs generated by PCs, including e-mails sent/received by desknet’s (a groupware product); and its good history of being installed in various companies IT systems.”
In 2005 April, when enforcement of the Private Information Protection Law began, Phiten Co., Ltd. (Phiten) was apprehensive that its customers’ private information might leak out through laptop PCs and USB memory devices used in the head office and/or in about 150 retail, “Phiten Shops”, which had spread nationwide. In 2007, after the company’s Operation Department System Management Section compared a number of log collection software products, they decided to install MylogStar (at that time, called “ALLWatcher”) which was provided by RUNEXY Corporation.
After installing MylogStar, the company became able to collect all kinds of logs generated by PC operations and was able to establish the foundations of private information protection. In addition, since the software can collect logs of laptop PCs and USB memory devices, the security structure against information leakage was complete. The workforce became security conscious toward PC operations and also became well motivated.
Problems and Results
Problems
- Need to protect the private information of “Phiten Shop” customers.
- Need to implement countermeasures to prevent information leakage from laptop PCs and USB memory devices.
- Need to collect and manage logs to detect contributing factors when information leakage cases occur.
Results
- Established the foundation of private information protection by collecting all logs from the company’s 600 PCs.
- Improved IT security by periodic inspections of laptop PCs and USB memory devices.
- Achieved compliance and motivated company members.
Installed MylogStar in 600 PCs Aiming at Perfect Protection of Customers’ Private Information
In 2007, the Phiten Operation Department System Management Section maintained and managed 600 desktop PCs and laptop PCs in total. The section had already introduced a content filtering tool to control Internet access as a security measure and prohibited employees from visiting irrelevant websites.

Regarding e-mail, it had collected sending logs in its Simple Mail Transfer Protocol (SMTP) server and conducted regular inspections on e-mail addresses and subject lines sent from the company’s PCs.
In addition, almost all the PCs already had anti-virus software installed. It could be said that the general security measures were complete.
However, Phiten, which had developed around 150 “Phiten Shops” all around the country, was apprehensive the customers’ private information could be leaked from laptop PCs and/or USB connecting memory devices used by their sales personnel. Implementing countermeasures against such incidents was an urgent business.
Under the circumstance, the Operation Department System Management Section started to a study of several software products to find out which one could enable the company to collect all logs including those generated by laptop PCs and USB-connecting memory devices so that they could find the contributing factors immediately if private information leaked out.
After the section compared competitive software products, they chose MylogStar which can collect 16 kinds of logs* (including optional functions) and installed the software in the company’s 600 PCs.
* English version can collect 13 kinds of logs
The Decisive Factors of MylogStar Were the Variety of Collectable Logs and the Easy Operation
MylogStar, which Phiten decided to introduce in the company’s IT system, can collect 13 kinds of ordinary logs and 3 other special logs using optional functions. The 13 types of logs normally collected include login/logoff, operations of applications, files a user accessed, filing operations, e-mails, accesses to the Internet, File Transfer Protocol (FTP), screen images at certain times, Transmission Control Protocol (TCP) sessions, and Windows events; and the 3 types of logs that optional functions collect are inventory information, e-mails sent/received by web mails, and messages sent/received by instant messaging.
Mr. Seiji Horiba of the Operation Department System Management Section said, “The reasons we chose MylogStar were that the software collects many types of logs including e-mails sent/received by desknet’s, a groupware we have used, and web mails, and the software also has a good history of installations.”
Ms. Fumiko Maki, also of the Operation Department System Management Section told us, in addition to the satisfactory kinds of collectable logs and the good history of being installed in 700 companies (200,000 clients in total), there were other reasons for choosing MylogStar;

“The Functions provided by the software are important; however, when choosing a certain product, the user interface is even more significant. If the software does not provide easy access, it is useless even though the software provides plenty of functions. On that point, MylogStar is more useful than other competitive products, and we are satisfied with the function that allows us to collect e-mail logs. Also, we can conduct log retrievals efficiently since the software can save frequently asked search criteria so that we do not need to input the same keywords again and again.”
In terms of cost effectiveness, the balance of the price of the product with the accuracy of log data the software collects made it the most competitive product, and that was one of the reasons for the installation.
Established an Secure Foundation of IT Security and Motivated the Workforce
At the beginning, Phiten set goals to be achieved with MylogStar as follows;
Purpose of the Installation
- Collecting all logs generated by all operations on all PCs to improve the security level.
- Detecting security threats as quickly as possible to implement countermeasures against the threats swiftly and on a top priority basis.
- Implementing the best security measures at a low cost.
- Focusing on sent/received e-mails, operations of applications, and filing operations, and carrying out periodic inspections.
After installation, what kind of results has MylogStar produced?
Installation Results
- One of the issues brought up was to improve security levels of laptop PCs that were used for marketing activities mainly outside the company’s network. Since MylogStar can collect all logs generated by all PCs including laptop PCs and manage them in one network, the company could achieve the security level that allows secure handling of customers’ private information. In addition, with the optional log collecting functions the software provides, the company became able to centrally manage the logs of their standalone PCs.
- No big problems have occurred yet. But a framework for dealing with security problems has been complete.
- MylogStar was able to provide Phiten the ability to collect all the logs the company requires to achieve a satisfactory security level at a low cost.
- By analyzing the e-mail logs the software collects, Phiten could get a handle on the actual number of spam mails and got rid of most of them by introducing an anti-spam program. Phiten also could learn the patterns of information sharing by staff through e-mail, and this gave the company good material for studying the more beneficial ways of information sharing.
- Phiten regularly retrieves logs of used applications to make sure that inappropriate applications, which are excluded from the company’s standard, are not used.
- Phiten became capable of observing the records of transfers and updates of files on shared folders by tracing the filing operation logs.
- Personnel’s motivation toward information security and compliance were improved after installing MylogStar.
- Windows event logs are managed centrally by MylogStar, so the company now can be aware of PC errors occurring in remote areas and utilize this information for maintenance and refinement.
- The Operation Department System Management Section submits log records, such as records of, active windows, to other departments for periodic inspections.
As observed above, the actual effects of installing MylogStar were even more profound than the company expected. Phiten is now planning to apply the alert functions and prevention/limitation of applications function that MylogStar can provide.
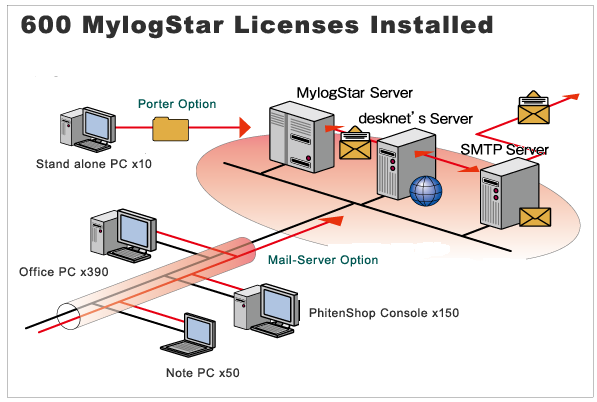
The Structure
The General Information about the Customer
Phiten Co., Ltd was established in 1983 and has developed businesses for the purpose of “Supporting People’s Health”. The company exploited various materials developed by its own technology for dispersing metals such as titanium, gold, and silver; water-soluble at nano-levels. By utilizing those metals’ qualities, the company succeeded in drawing out the “natural healing ability”, which humans originally possess, and to relax human bodies. Phiten sells products which are related to sports such as: Phiten necklaces and bracelets (Rakuwa necklaces and bracelets), tapes, jells, and aqua-titanium supporters. In addition, the company provides various kinds of products and services such as: health food and goods, supplements, drinking water, cosmetics, hair care products, and medical devices. Three of them including “The Phiten titanium necklaces (Rakuwa necklaces)” are licensed by Major League Baseball (MLB) in the U.S. as official goods.
URL : http://www.phiten.com



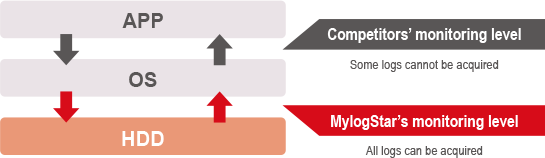
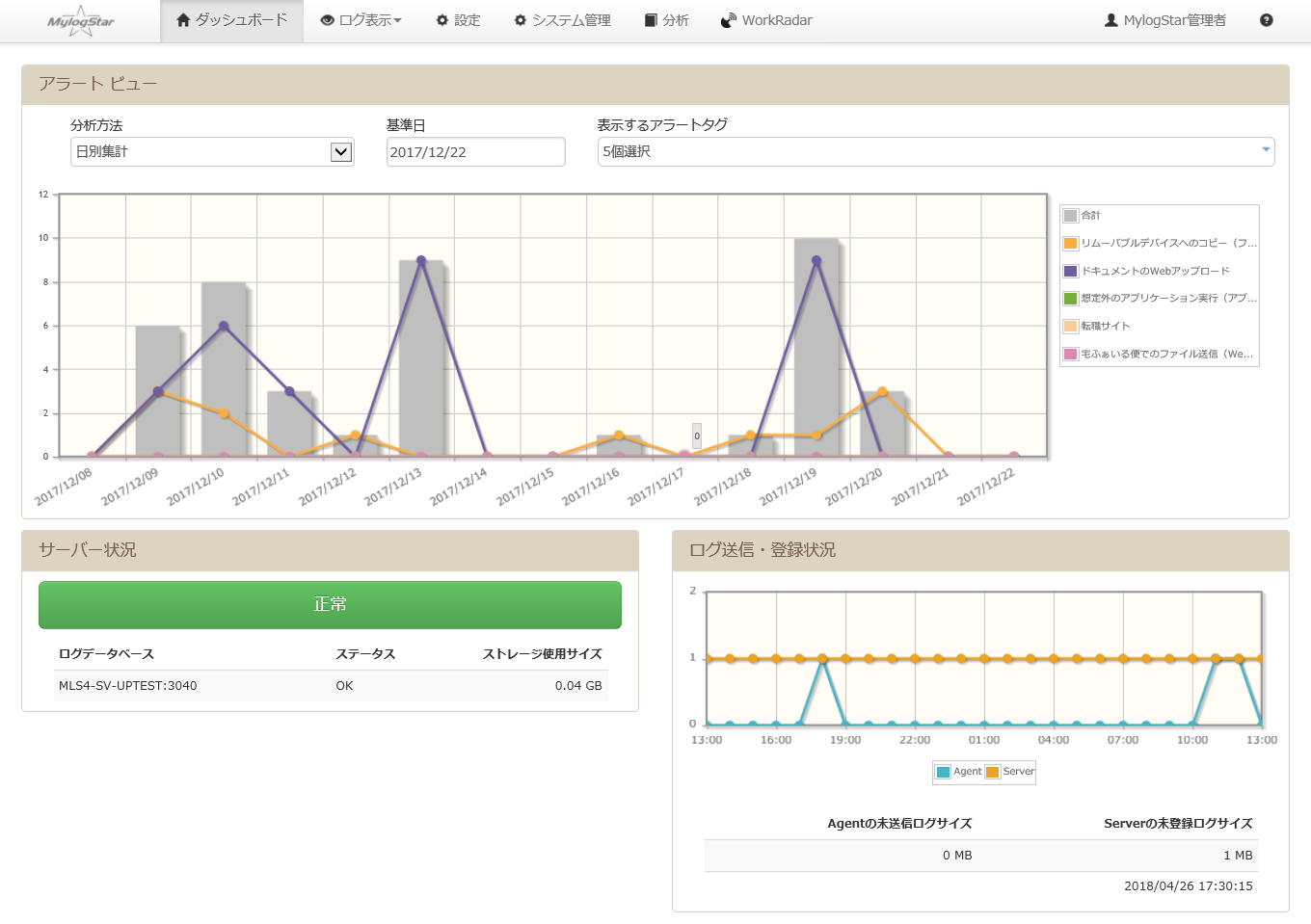
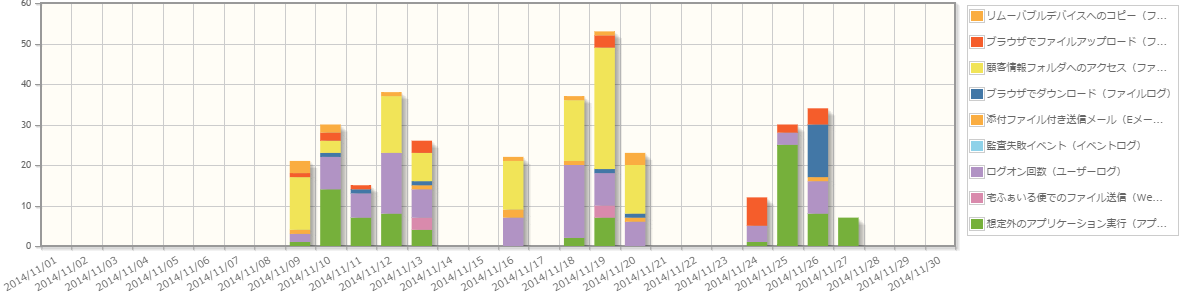
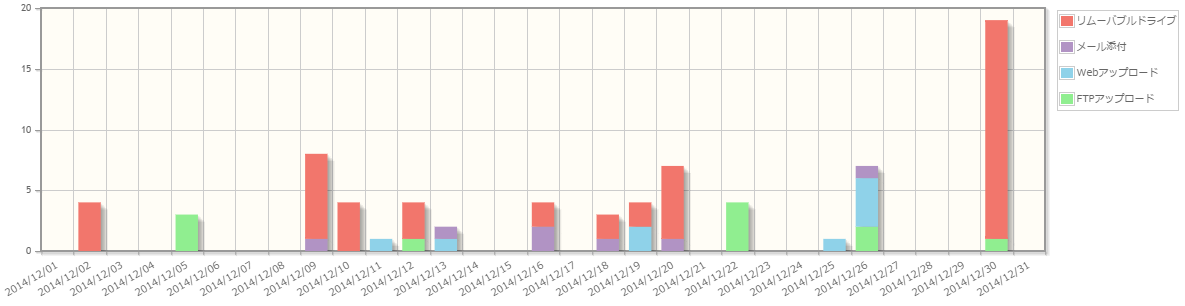
 Acquire information about 15 types of client operations
Acquire information about 15 types of client operations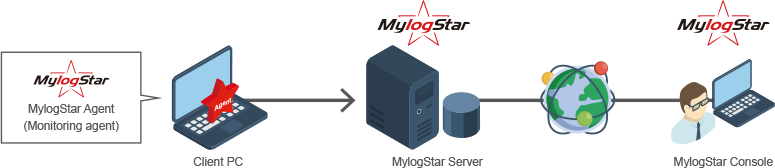
 Functions
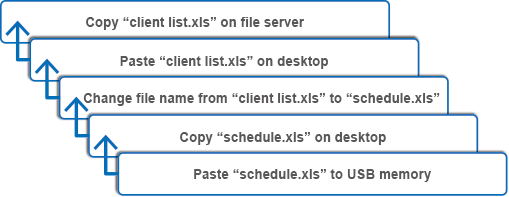
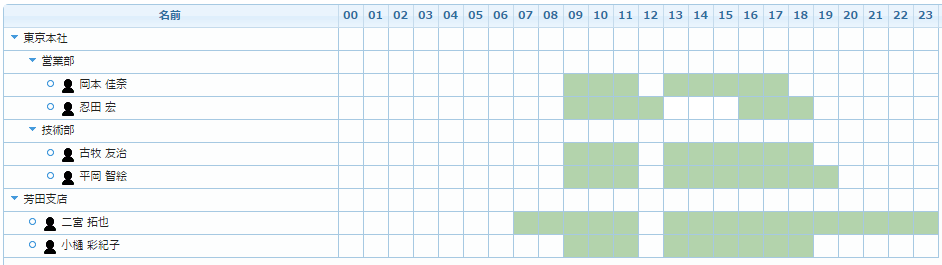
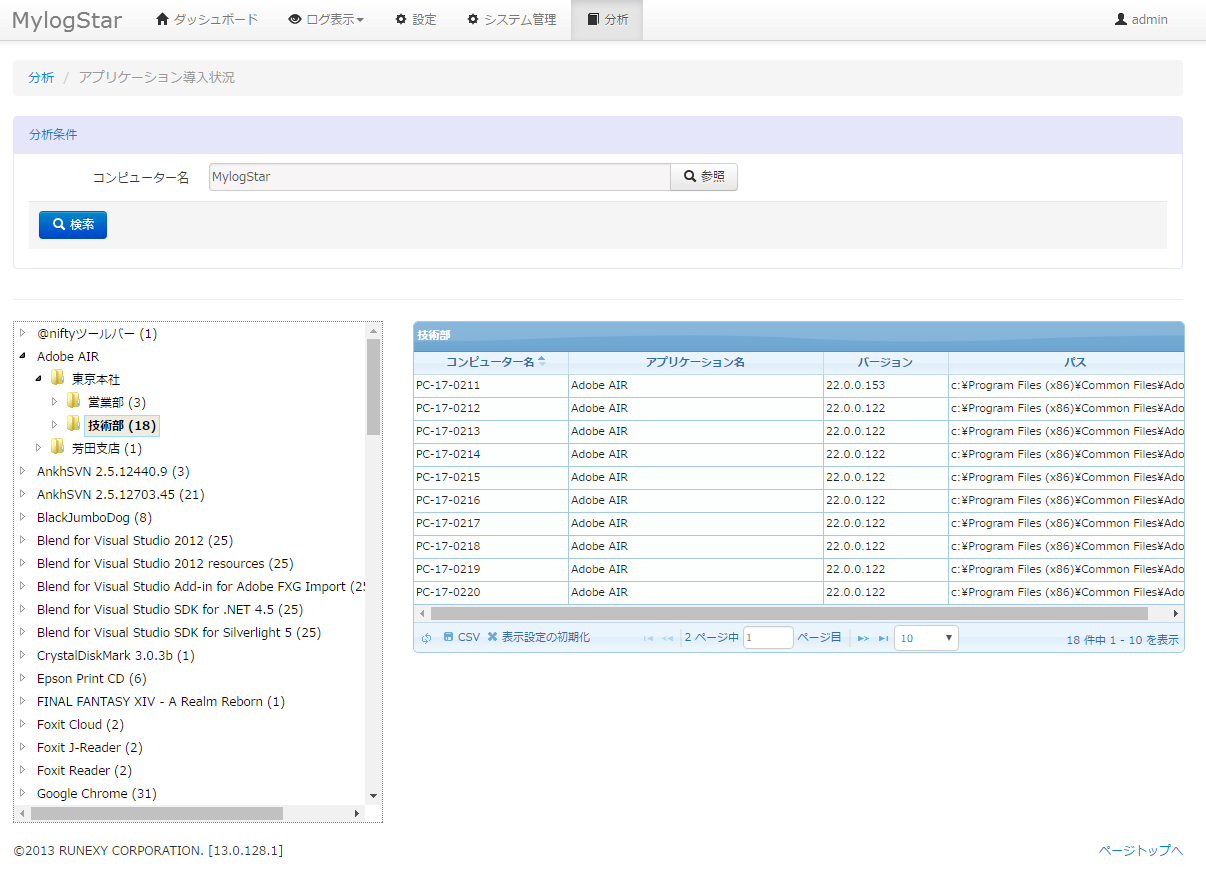
Functions Trace function
Trace function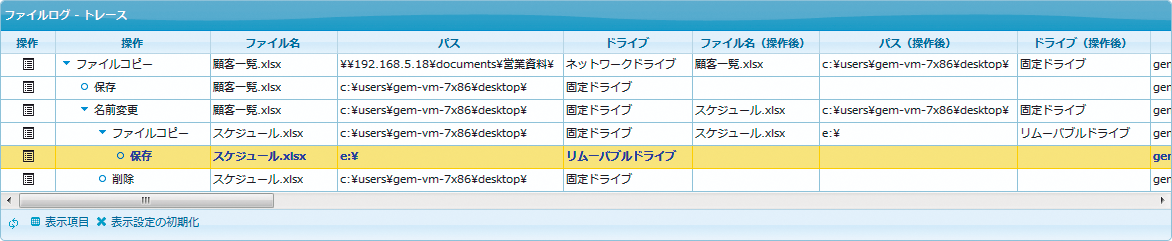





 NEXT ・・・
NEXT ・・・